对 Agent 进行加壳防护,防止被篡改。采用加密传输与服务端通信,保证数据安全
通过 50000+ 台服务器的运行实践,稳定性高达 99.998%。2 分钟内离线自动重启机制,保障系统始终处于监测状态
正常的系统负载情况下,CPU 占用率 <1%,内存占用 <40M,消耗极低。在系统负载过高时,Agent 会主动降级运行(CPU 占用率 <1%),严格限制对系统资源的占用,确保业务系统正常运行
集成包括小红伞、ClamAV 等国内外多个主流的病毒查杀引擎。具有自主研发的大数据分析、机器学习和模式行为等多种检测模型,为用户提供全面和实时的后门检测和防护能力。实时监控、检测分析、多渠道告警、高效处理的安全闭环能力
持续关注监管政策,助力企业达到监管要求。自定义检查标准,满足不同检查基准场景
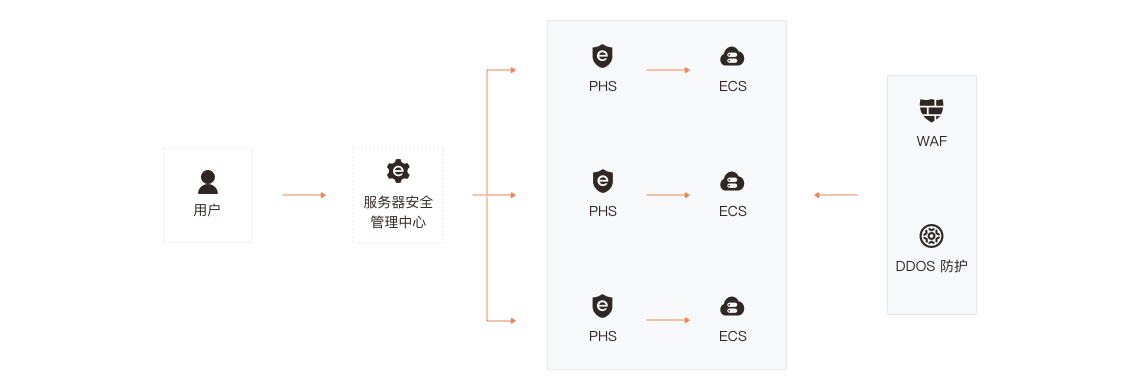
为平安云服务器提供安全防护,采用的 Adaptive Security 架构是 Gartner 提出的面向未来十年的企业安全架构,能够在复杂和变化的环境下有效抵御高级攻击,是整个安全行业的发展方向。
其创新之处在于:
1)将安全视角转移到防火墙之后的业务系统内部,强调基于业务、自内而外地构建安全体系
2)将安全从传统的安全事件防护变成一项持续安全响应和处理过程,从多个维度持续地保护了企业安全
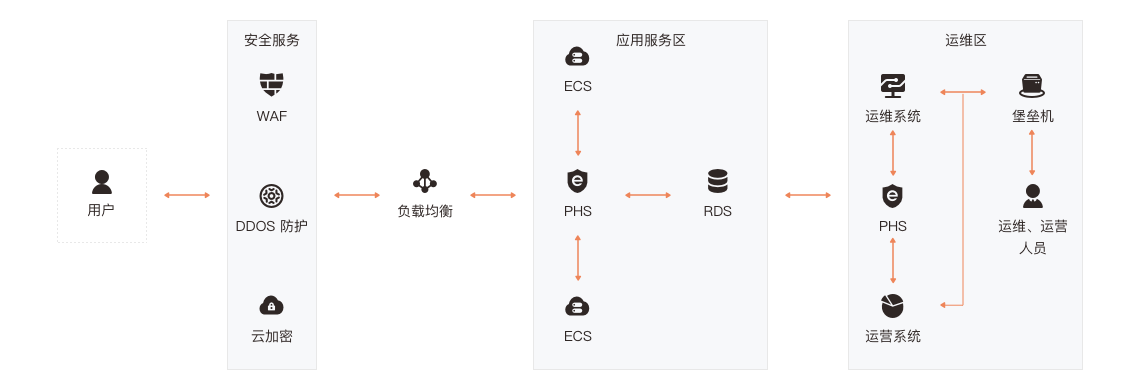
支持满足合规中提到的能够检测到对重要节点进行入侵的行为,防范恶意程序获取或篡改敏感信息,并在发生严重入侵事件时提供报警。以及支持对后门、木马、蠕虫、webshell 等恶意代码的静态检测和行为检测,并对检测出的恶意代码进行控制和隔离等要求。提供合规基线的功能,方便用户自查。
资产清点,致力于帮助用户从安全角度自动化构建细粒度资产信息,支持对业务层资产精准识别和动态感知,让保护对象清晰可见。使用 Agent-Server 架构,提供 10 余类主机关键资产清点,200 余类业务应用自动识别,并拥有良好的扩展能力
风险发现致力于帮助用户精准发现内部风险,帮助安全团队快速定位问题并有效解决安全风险,并提供详细的资产信息、风险信息以供分析和响应
入侵检测提供多锚点的检测能力,能够实时、准确地感知入侵事件,发现失陷主机,并提供对入侵事件的响应手段
合规基线构建了由国内信息安全等级保护要求和 CIS(Center for Internet Security)组成的基准要求,涵盖多个版本的主流操作系统、Web 应用、数据库等。结合这些基线内容,一方面,用户可快速进行企业内部风险自测,发现问题并及时修复,以满足监管部门要求的安全条件;另一方面,企业可自行定义基线标准,作为企业内部管理的安全基准